来源:https://github.com/xerof4ks/heapwn/tree/master/rhme3
初步了解
1 | root@kali:~/learn/heapwn/rhme3# ./main.elf |
堆的题目基本都是选择菜单,这里可以添加,删除,选择,编辑,展示球员,还可以显示队伍,功能看着很多啊
首先玩玩一下这个游戏,便于后期逆向一些数据结构
1 | Your choice: 1 |
上面就是球员这个结构有什么信息,第一个free slot就相当于球员的id,这个不用我们输入
remove就删除咯
1 | Your choice: 2 |
select会输出球员的信息
1 | Your choice: 3 |
edit当前的palyer,基于上面的select
1 | Your choice: 4 |
show palyer,这个显示的是select的player
1 | Your choice: 5 |
show team会将所有球员信息打印出来
1 | Your choice: 6 |
经过对add_player的逆向,可以推出palyer的结构
1 | struct palyer{ |
编写add_palyer查看内存结构
1 | def add_palyer(name, attack = 1, defense = 2, speed = 3, precision = 4): |
查看内存如下,大小为0x20,
1 | gdb-peda$ x /20g 0x1675010-0x10 |
添加两个球员
1 | gdb-peda$ x /60gx 0x0000000001759010 |
了解得差不多了,开始吧
查找漏洞
看下delete,判断index不能大于10,且全局players数组不为0,而且delete后将相应的players索引置0,所以不存在double free,free的时候首先将name释放,再释放整个palyer
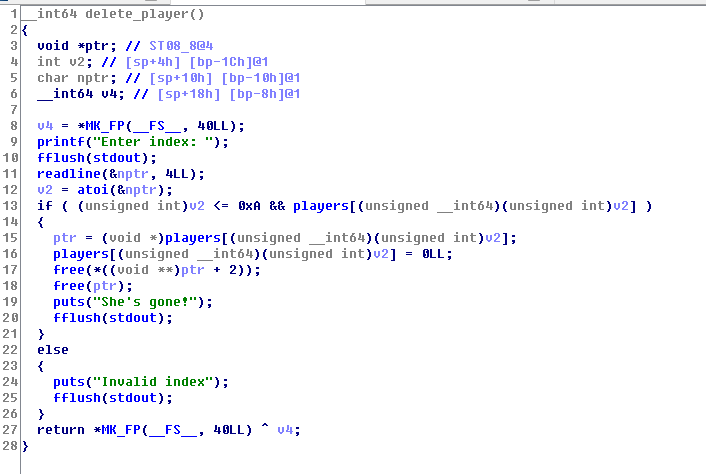
那看看释放后能否重用,看看show palyer,因为delete没将selected置0,导致可以重用,这可以导致信息泄露
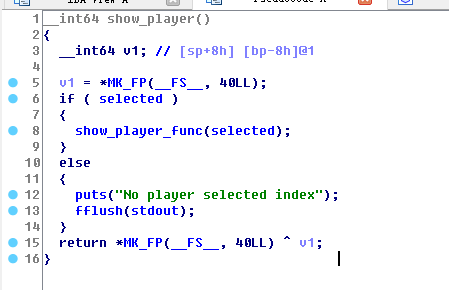
再有edit可以导致任意地址写漏洞
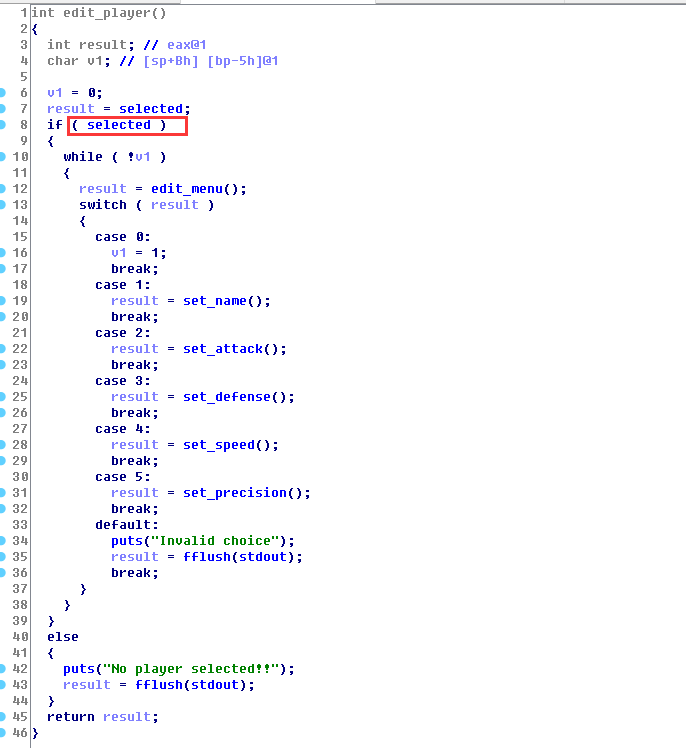
那怎么占位呢(下面图说的0x17不一定,我们0x16,0x15等也能占位,差不多大小就行)
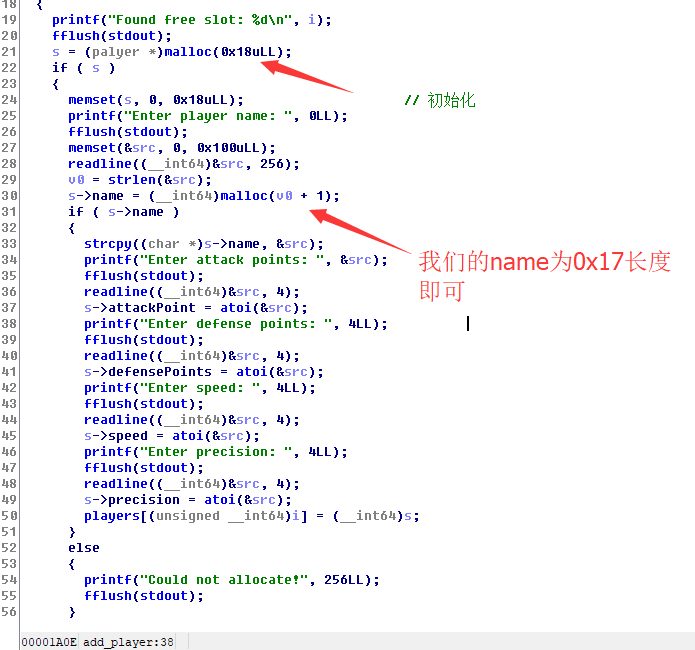
就是创建两个palyer,都free掉,再创建一个palyer即可占位,用name占第二个palyer的结构
还有我们下面写got的话有两个目标,一个atoi,一个strlen,不过atoi的话传入的参数只有四字节,只能传个sh过去了,strlen也是可以的,留给大家尝试,就不贴出来了
exp
1 | # -*- coding: utf-8 -*- |


